
Author: Nanj
https://app.hackthebox.com/sherlocks/Campfire-2/play
Forela’s Network is constantly under attack. The security system raised an alert about an old admin account requesting a ticket from KDC on a domain controller. Inventory shows that this user account is not used as of now so you are tasked to take a look at this. This may be an AsREP roasting attack as anyone can request any user’s ticket which has preauthentication disabled.
The AS-REProasting attack shares similarities with the Kerberoasting attack in its method of targeting Kerberos authentication vulnerabilities. Specifically, it exploits user accounts that have the “Do not require Kerberos preauthentication” property enabled. By requesting an authentication service (AS-REQ) for such accounts, an attacker can obtain a crackable hash (AS-REP) of the account’s password. The effectiveness of this attack hinges on the complexity and strength of the user’s password; weaker passwords are more susceptible to being cracked, potentially granting unauthorized access to the account and associated resources.
The Attack:
The AS-REProasting attack, like the Kerberoasting attack, targets weaknesses in Kerberos authentication mechanisms. Specifically, it exploits user accounts with the “Do not require Kerberos preauthentication” property enabled. By leveraging this misconfiguration, attackers can request an authentication service response (AS-REP) for these accounts and obtain crackable hashes. The attack’s success largely depends on the complexity and strength of the targeted user’s password; weaker passwords are more vulnerable to cracking, potentially leading to unauthorized access to sensitive systems and data.
To obtain crackable hashes, tools like Rubeus can be used with the asreproast action. When executed without specifying a target username, Rubeus will enumerate and extract hashes for all user accounts configured without Kerberos preauthentication. This streamlined approach simplifies the identification of vulnerable accounts within the domain.
Other tools that can facilitate AS-REProasting include:
- Impacket’s GetNPUsers.py: A Python script designed to identify and retrieve AS-REP hashes for accounts with preauthentication disabled.
- Kerbrute: Useful for brute-forcing and enumeration of Kerberos accounts, including identifying those susceptible to AS-REProasting.
- PowerView: A PowerShell tool that can help identify accounts with weak Kerberos configurations, including preauthentication settings.
These tools provide flexible and powerful options for enumerating vulnerable accounts and obtaining hashes for subsequent offline cracking. Proper use of these tools, combined with password cracking utilities like Hashcat or John the Ripper, can significantly aid in this attack vector.
Detection:
Executing Rubeus or similar tools for AS-REProasting generates Event ID 4768, signaling a Kerberos Authentication Service ticket request. This event is common, as it’s logged for every Kerberos authentication, making it noisy. However, it includes the IP address of the system where the request originated, enabling correlation of known good logins with potential malicious activity.
For environments with roaming users, correlating by IP may be challenging. Monitoring authentication attempts by VLAN can be more effective, allowing detection of requests from unexpected network segments.
Let’s begin the investigation. First, we will parse the Security.evtx file to a CSV format using EvtXCmd.exe, and then open it in TimelineExplorer.

For Task 1: When did the ASREP Roasting attack occur, and when did the attacker request the Kerberos ticket for the vulnerable user?
Upon filtering logs for Kerberos-related activities, I identified multiple false positives involving service accounts with $ in their names and using typical encryption types. These service accounts are expected in normal operations and do not indicate malicious behavior.
However, one activity stood out as suspicious and potentially malicious. The log entry below highlights a request made by a normal user account (arthur.kyle) within the forela.local domain. The ticket was encrypted using RC4-HMAC (type 0x17), which is highly unusual for standard Kerberos activities and often associated with attacks like Kerberoasting or AS-REProasting.

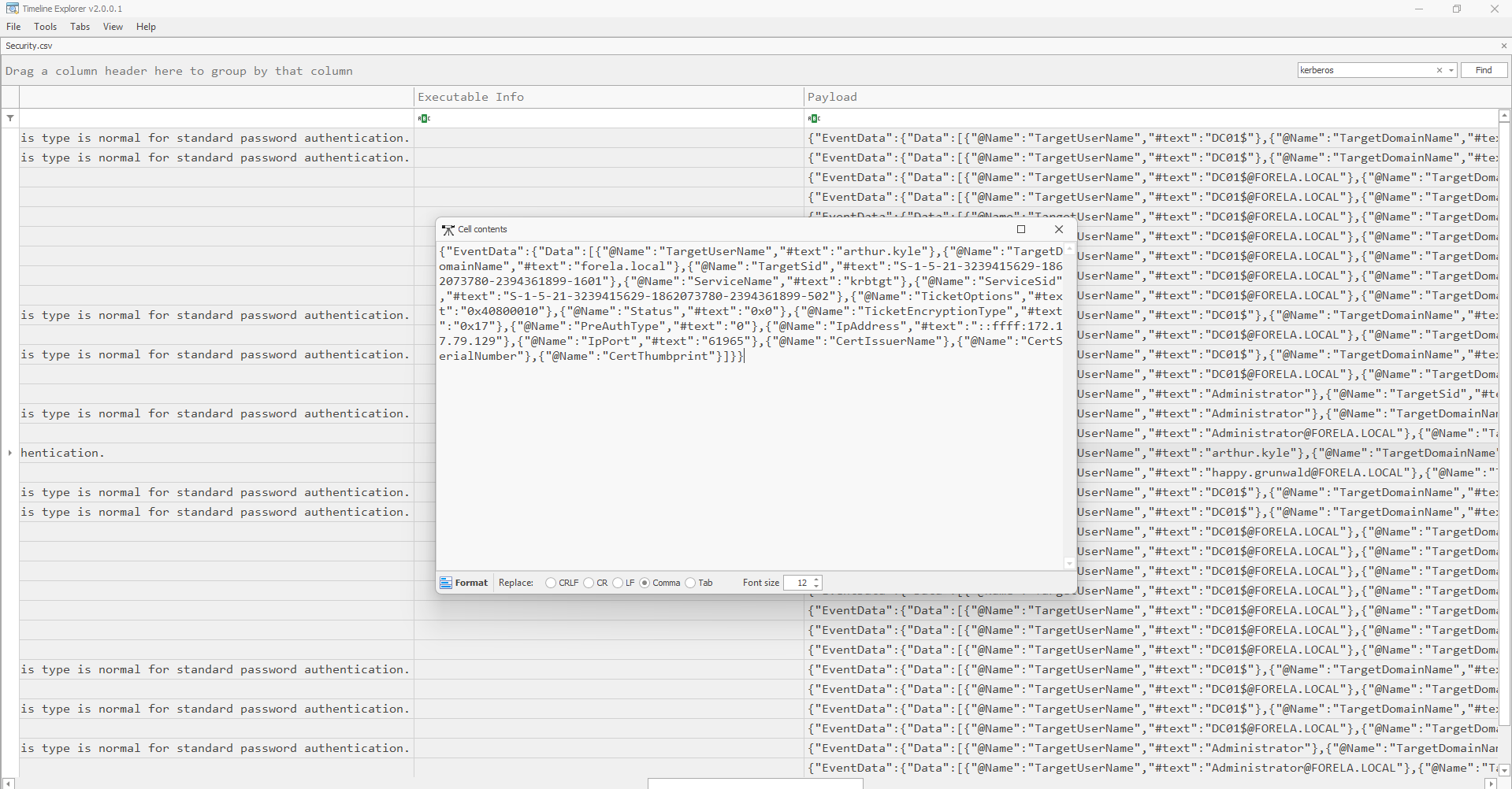
- User Account:
arthur.kyle - Domain:
forela.local - Ticket Encryption Type:
0x17 (RC4-HMAC) - Service Name:
krbtgt - IP Address:
172.17.79.129 - Port:
61965 - Ticket Options:
0x40800010
Given the uncommon use of RC4-HMAC for this user account, combined with the originating IP and ticket options, this activity is confirmed as malicious. This discovery aligns with typical behaviors seen in Kerberos-based attacks, specifically targeting encryption weaknesses for offline hash cracking.
Task 1 answer: 2024-05-29 06:36:40
For questions 2–4, we can answer them using the screenshot and the investigation from Task 1.
Task 2: Please confirm the User Account that was targeted by the attacker.
Task 2 Answer: arthur.kyle
Task 3: What was the SID of the account?
Task 3 Answer: S-1-5-21-3239415629-1862073780-2394361899-1601
Task 4: It is crucial to identify the compromised user account and the workstation responsible for this attack. Please list the internal IP address of the compromised asset to assist our threat-hunting team.
Task 4 answer: 172.17.79.129
Task 5: We do not have any artifacts from the source machine yet. Using the same DC Security logs, can you confirm the user account used to perform the ASREP Roasting attack so we can contain the compromised account/s?


hrough log analysis, Event ID 4769 provided critical insights. It showed the same IP address (172.17.79.129) linked to the earlier anomalous event, confirming this machine as the source of the attack. This event identifies the arthur.kyle account as the victim, rather than the attacker, suggesting an initial compromise followed by lateral movement.
Further analysis revealed a subsequent event where the happy.grunwald@FORELA.LOCAL account was used from the same IP. This account, while not showing any overtly malicious behavior, requested a service ticket from DC01$, part of normal domain operations. Its presence on the suspect machine strongly suggests it was leveraged by the attacker to pivot and escalate privileges.
- Victim Account:
arthur.kyle - Suspect Account:
happy.grunwald@FORELA.LOCAL - Attacker’s IP Address:
172.17.79.129 - Service Name:
DC01$ - Ticket Encryption Type:
0x12 - IP Port:
61975
Task 5 Answer: happy.grunwald
Thanks for Reading! We hope you enjoy this writeup, Happy Grinding Shinkens!

Leave a comment