Author: Aaron Q
Introduction
In a Security Operations Center (SOC), certain platforms are treated with absolute confidence. VirusTotal is the Bible of Threat Intelligence because analysts and SOAR playbooks query it daily to enrich hashes and triage alerts. Consequently, VirusTotal is almost never blocked as it is an essential tool for investigations, and blocking access to this domain would be functionally damaging to the incident response workflow.
As being in a defensive role, I have noticed that this reliance can be quickly overlooked if weaponized. This dependency creates a major operational blind spot where treating VirusTotal as a known good destination provides a possible opening for the very threats defenders are hunting. When a destination is whitelisted by default, it becomes a significant gap in network egress monitoring.
Leveraging certain VirusTotal API endpoints allows for the transformation of a primary security tool into a Dead Drop Resolver (T1102.001). By utilizing the comments section, it is possible to establish a persistent channel for Command and Control (C2) and data exfiltration.
The Motivation
Over the past year, several reports have highlighted a significant shift in attacker methodology: the direct abuse of the tools defenders utilize. Notable examples include the weaponization of Velociraptor for incident response evasion and the emergence of “Bring Your Own Installer” (BYOI) attacks that leverage the SentinelOne installer. These techniques succeed because they exploit the inherent trust placed in signed binaries and authorized security utilities.
The evolution of tool abuse is not limited to local binaries. The following experiment reveals a vector for abuse at the network level by leveraging the VirusTotal API as a communication layer. This demonstrates how a global, high-trust security service can be transformed into a persistent exfiltration and tasking resolver, moving the threat deep into the defensive infrastructure of an organization.
The API Endpoint Abuse
Note: The following content is provided strictly for educational purposes and defensive research. The goal of this Proof-of-Concept is to assist analysts in identifying and mitigating non-traditional C2 channels.
The VirusTotal API allows organizations to automate file lookups and hash enrichment at scale. It is primarily used to integrate VirusTotal data into security tools like EDRs and SIEMs, ensuring that detection pipelines can query file reputations automatically. One specific feature of this API is the Comments endpoint, which allows users to programmatically post and retrieve technical notes or community feedback associated with a specific file hash.
Below is a sample API endpoint requests for posting and retrieving a comment:
# Post a commentcurl --request POST \ --url https://www.virustotal.com/api/v3/files/id/comments \ --header 'accept: application/json' \ --header 'content-type: application/json' \ --data '{ "data": { "type": "comment", "attributes": { "text": "Lorem ipsum dolor sit ..." } }}'# Retrieve commentscurl --request GET \ --url 'https://www.virustotal.com/api/v3/files/{id}/comments?limit=10' \ --header 'x-apikey: <your_api_key>' \ --header 'accept: application/json'This functionality provides the necessary infrastructure for a persistent communication channel. By using the API to post and read structured JSON data within the comments section, an operator can utilize VirusTotal as a middleware for Command and Control (C2). Because the agent is communicating directly with a trusted API and domain, the traffic blends in with the standard lookups performed by a SOC.
The Implementation
This experiment utilizes two separate VirusTotal channels as its core backbone, each represented by a unique and unknown file hash. Using these hashes ensures that it is not flagged by existing signatures or cross-referenced in other threat intelligence databases, thus adding a layer of security in the activity.
The architecture is divided into two functional paths:
- Tasking Channel (Hash A): This hash acts as the primary repository for commands. The operator posts instructions here as JSON-encoded comments. The agent periodically polls this hash to retrieve new tasks.
- Output Channel (Hash B): Once a task is executed, the agent sends the results to this second, distinct hash. Separating the inbound commands from the outbound data prevents a high-volume comment stream on a single file, which might trigger suspicious activity.
To make things more challenging for defenders in case the file hashes are discovered, every time a task is finished, any output references to it are removed using the delete comment API request. This cleanup mechanism ensures that even if an analyst gains access to the hash, the historical record of commands and exfiltrated data is systematically wiped, leaving little to no forensic trail on the platform.
Below is the sample API request for deleting a comment:
curl --request DELETE \ --url https://www.virustotal.com/api/v3/comments/{id} \ --header 'x-apikey: <your_api_key>' \ --header 'accept: application/json'The Proof-Of-Concept
To test this PoC, I am utilizing a custom agent executed on a target machine acting as the victim, and a server-side script used to issue commands and ingest results. While this setup works incredibly well for staying hidden, it is important to address the limits of the platform and how they can actually be turned into tactical advantages. The current experiment utilizes the free tier of the VirusTotal API, which carries specific usage rules:
While a traditional, high-volume C2 might see these as hurdles, a real-world perspective recognizes these limits as built-in stealth. This slow pace naturally mimics the occasional, automated queries generated by a SOC’s own security tools or an analyst’s manual investigation. By staying within these quotas, the C2 traffic looks exactly like normal administrative work, making it harder to pick out of a crowd using standard monitoring tools.
Below is a screenshot of the task sent to one of the file hashes for the agent to execute. In this instance, I issued an ipconfig /all command via PowerShell. However, this method is not recommended for actual operations, as it will likely trigger alerts for processes spawning cmd.exe or powershell.exe. It is left to the reader to experiment with more stealthy ways of executing commands and retrieving data without relying on these noisy, monitored processes:
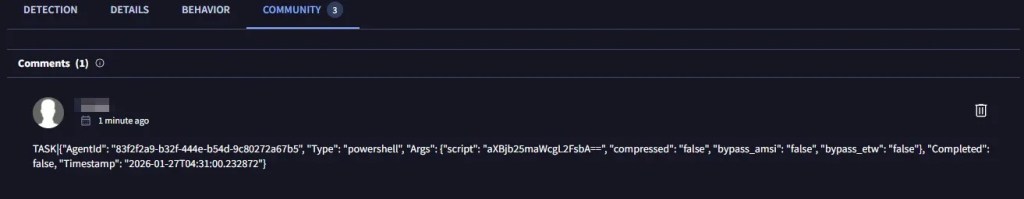
The following output shows the data successfully received by the server-side script. It is critical to note that both the server-side controller and the deployed agent must utilize a matching Agent ID to properly synchronize tasking and exfiltration. This unique identifier ensures that commands are directed to the correct ID and that the resulting data is mapped accurately, even when multiple agents are operating across the same infrastructure:
To maximize the potential of this experiment, I also integrated an execute-assembly capability. This addition allows for the in-memory execution of .NET binaries, enabling the agent to run complex post-exploitation tools without ever writing them to the disk.
The Advantageous Trade-Off
A significant consideration in this experiment is the impact on data transfer speeds. Because the architecture relies on the free VirusTotal API, we are bound by its strict rate limits. This affects not just the execute-assembly capability, but all large data sets being exfiltrated or retrieved.
To remain operational within these constraints, the framework utilizes data chunking. Large files or complex command outputs must be broken down into small, manageable fragments to fit within individual API comments.
While this makes the process objectively slow, the delay is a deliberate tactical choice for several reasons:
- Low Volume Traffic Evasion: Rapid and high-volume data spikes are a primary trigger for modern SOC alerts. By throttling data out in chunks, the agent stays well below the threshold of anomaly detection.
- The Long-Haul C2 Strategy: This architecture is specifically designed for long-haul C2 operations, where the objective is to maintain a persistent connection over weeks or months. In this context, the stability and “trusted” status of the communication channel are far more important than how fast the data moves.
- Blending with Administrative Baselines: The slow pace mimics the standard behavior of security tools performing periodic telemetry lookups or analysts conducting manual OSINT activity. In a real-world scenario, an operator would rather take days to exfiltrate a sensitive file invisibly than take three seconds and trigger an immediate incident response.
The Defensive Delusion
The success of this experiment highlights a fundamental failure in static defense models. Many SOCs operate on a hollow definition of safety where a “green” reputation score effectively ends the investigation. If a domain is reputable, it is ignored. If a binary is signed, it is trusted. If a tool belongs to the security stack, it becomes invisible.
Defenders have spent so much time building walls against “known bad” indicators that they have forgotten how to monitor the “known good”. This creates a massive, unmonitored playground for sophisticated actors.
The irony is that the very tools used to hunt threats have become the most effective way to hide them. While analysts are busy chasing high-fidelity alerts from their SIEM/EDR, they are often blind to the fact that third-party security APIs can be utilized to facilitate a quiet, persistent exfiltration channel.
What Lies Ahead
VirusTotal is only the beginning. These Dead Drop Resolver techniques have been around for a long time, famously documented by the Living Off Trusted Sites (LOTS) Project. However, you will notice that security tools are largely absent from that list. The tradecraft itself is not new; the channel has simply shifted. We are now seeing any security platform that offers public-facing API endpoints for community engagement being converted into a Command and Control (C2) bridge. This turns the defender’s own trusted infrastructure against them. As long as these endpoints are whitelisted by default, they remain open invitations for long-haul persistence.

Leave a comment